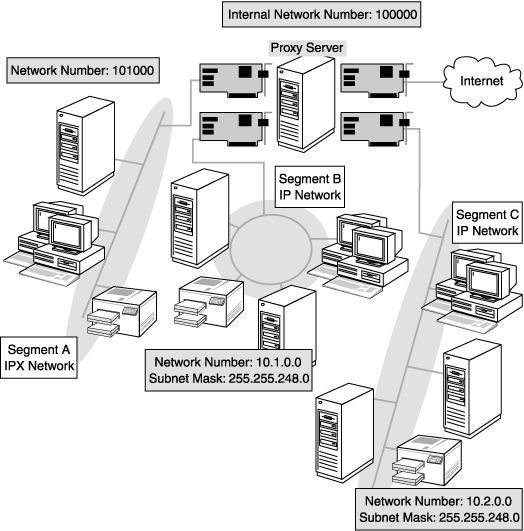
Proxy is a computer acting as gateway in between a local network (e.g., all the computers at one company or in one building) and a larger-scale network such as the Internet. Proxies are used for better performance and securing the local network Often, proxies monitor users access to the outside network.
Proxy Server operates by sitting between the local network and outside network. All incoming data enters through one port and is forwarded to rest of the network through another port. Blocking direct access in between two networks, proxy servers make it difficult for hackers to get access to local network.
An organization is represented by a single proxy in the outside network irrespective of the number of computers in the internal network. All requests to outside resources are catered by this single server. The responses from outside are also received by it and given to respective requesting computers. This gives the outside world one single point to access the internal network instead of multiple points of entry representing each computer in the network. This makes safeguarding the internal network much easier.
Proxies may also be configured to cache the requested pages. As a user accesses a outside resource, a temporary copy is saved locally. The next time a user requests the same resource, the proxy can serve the local copy, improving performance.
Some Other Uses of Proxy Servers:
We covered above the utilization of proxy in a LAN. Very commonly, people use proxy servers for multiple other purposes as well. Such as, to access content which is restricted to users of particular regions. For example, users in Africa trying to see Hulu will not be allowed to. But by connecting to Hulu through a US Proxy, they can bypass that restriction. The same thing applies if you live in the U.S. and wanting to access BBC content through their iPlayer. They will require to access through a proxy with UK IP address .
Extremely common use of Proxies is to circumvent surfing restrictions at places where access to internet is blocked.
Criminals also make heavy use of proxies to obscure their actual locations. They can even chain proxy servers together to increase the difficulty of being tracked. . Malware roaming the net in search of unpatched systems, would find only the proxy which usually will be well prepared against threats. Security people also use Proxies. While trying to break into the criminal underground, the last thing you want is to give them your home address. Similarly, privacy concious people prefer to use anonymous web proxies to safeguard their private information. Accessing internet without anonymous proxies discloses ones IP address and other sensitive information to the open . This information can be used by hackers to hack into computers and get all the information stored on the computer.
Web based Proxy to Bypass Restrictions:
Web Proxy accepts required URLs using a Web form in the user's browser window, processes the request, and returns the results in the browser window. Consequently it is used to bypass internet censors and fetch the blocked resource to the user.
Web based proxies might or might not hide the user's IP address based on how the proxy has been set up. To ensure online safety, usually you may not leave it to these free web based proxies. Privacy conscious people use paid proxies or VPNs (Virtual Private Networks). VPNs charge quite nominally. The one which I personally use to safeguard my data on virtual world is VPN Ace. VPNAce offer free trial to test run the service before buying. Click here to test the best and reasonably priced VPN.
In case do not want to go with the paid option, you may use our network of web based proxies which are totally anonymous.
Free Anonymous web Proxy